1. In electronic systems, a heat sink is a passive heat
exchanger that cools a device by dissipating heat into the surrounding medium.
In computers, heat sinks are used to cool central processing units or graphics
processors. A heat sink is what covers the microprocessor. It is needed because as the microprocessor does millions of calculations per second it gets very hot. The heat sink is used to cool down your computer by passing on the heat from a conductive gel to a piece of metal.

2. The initials CPU stand for central processing unit.
The control unit is a component of a computer's CPU that
directs operation of the processor. It tells the computer's memory,
arithmetic/logic unit and input and output devices how to respond to a
program's instructions. It is the main core of a computer where every command runs through and is routed to its appropriate location.
The ALU (Arithmetic and Logic unit) carries out mathematical and logical computations.
For example:
• Addition
and subtraction
• Multiplication and division
• Logical tests
• Comparisons
• Multiplication and division
• Logical tests
• Comparisons
Registers are memory locations within the CPU itself for
storing data and instructions.
They are designed to be quickly accessed for fast data
retrieval.
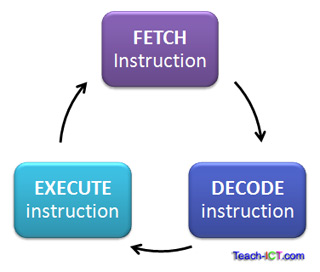
3. The fetch-decode-execute cycle.
Fetch:
the first step the CPU carries out is to fetch some data and instructions from the main memory and then store them in it's own internal temporary memory areas. These memory areas are called registers.
Decode:
the next step is for the CPU to register what it has just fetched. The CPU is designed to understand a specific set of commands. These are called 'instruction set' of CPU. Each CPU has a different instruction set. The CPU decodes the instruction and prepares various areas of the chip in readiness of the next step.
Execute:
This is when data processing actually takes place. The instruction is carried out upon the data. Once it has been carried out, it is stored in another register. Once the execute stage is complete, the CPU sets itself up to repeat the cycle.
4. List three common household devices, other than computers, which contain microprocessors:
5.
The control unit:
It controls and monitors the hardware attached to the system to make sure that the command given to it by the application software are used. It controls the input and output of data so that the signals go to the right place at the right time. It controls the flow of data within the CPU (The fetch-decode-execute cycle)


3. The fetch-decode-execute cycle.
Fetch:
the first step the CPU carries out is to fetch some data and instructions from the main memory and then store them in it's own internal temporary memory areas. These memory areas are called registers.
Decode:
the next step is for the CPU to register what it has just fetched. The CPU is designed to understand a specific set of commands. These are called 'instruction set' of CPU. Each CPU has a different instruction set. The CPU decodes the instruction and prepares various areas of the chip in readiness of the next step.
Execute:
This is when data processing actually takes place. The instruction is carried out upon the data. Once it has been carried out, it is stored in another register. Once the execute stage is complete, the CPU sets itself up to repeat the cycle.

4. List three common household devices, other than computers, which contain microprocessors:
- Mobile phones
- Calculators
- Watches
5.
The control unit:
It controls and monitors the hardware attached to the system to make sure that the command given to it by the application software are used. It controls the input and output of data so that the signals go to the right place at the right time. It controls the flow of data within the CPU (The fetch-decode-execute cycle)

Arithmetic Logic Unit:
The ALU performs mathematical, logical, and decision
operations in a computer and is the final processing performed by the
processor.
